Search results
Appearance
- The colon, :, is a punctuation mark consisting of two equally sized dots aligned vertically. A colon often precedes an explanation, a list, or a quoted...44 KB (4,683 words) - 09:42, 1 July 2024
- DisplayPort (DP) is a proprietary digital display interface developed by a consortium of PC and chip manufacturers and standardized by the Video Electronics...155 KB (12,489 words) - 05:04, 23 June 2024
- In computer science, a tree is a widely used abstract data type that represents a hierarchical tree structure with a set of connected nodes. Each node...17 KB (2,155 words) - 01:53, 3 July 2024
- A file format is a standard way that information is encoded for storage in a computer file. It specifies how bits are used to encode information in a digital...33 KB (4,557 words) - 06:35, 2 July 2024
- Mix networks are routing protocols that create hard-to-trace communications by using a chain of proxy servers known as mixes which take in messages from...17 KB (2,672 words) - 12:18, 11 June 2024
- EndeavourOS is a Linux distribution based on Arch Linux. EndeavourOS uses the same rolling release schedule as Arch Linux, but periodically does "releases"...9 KB (742 words) - 23:19, 30 June 2024
- Teletex was ITU-T specification F.200 for a text and document communications service that could be provided over telephone lines. It was rapidly superseded...3 KB (411 words) - 15:48, 20 October 2023
- Automatic summarization is the process of shortening a set of data computationally, to create a subset (a summary) that represents the most important or...52 KB (6,825 words) - 14:16, 11 June 2024
- An Internet entrepreneur is an owner, founder or manager of an Internet-based business. This list includes Internet company founders and people brought...49 KB (134 words) - 11:01, 16 May 2024
- Solaborate /ˈsōˈlabəˌrāte/ is a communication and collaboration platform for professionals and consumers. It allows them to do video calls, share documents...6 KB (514 words) - 16:47, 20 April 2024
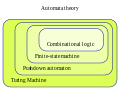
- In the theory of computation, a branch of theoretical computer science, a pushdown automaton (PDA) is a type of automaton that employs a stack. Pushdown...26 KB (4,019 words) - 07:17, 18 April 2024
- BASICODE was a computer project intended to create a unified standard for the BASIC programming language. BASIC was available on many popular home computers...18 KB (2,532 words) - 14:48, 16 May 2024
- Data publishing (also data publication) is the act of releasing research data in published form for use by others. It is a practice consisting in preparing...18 KB (2,051 words) - 05:58, 15 April 2024
- A system programming language is a programming language used for system programming; such languages are designed for writing system software, which usually...12 KB (888 words) - 02:30, 3 June 2024
- Magic is an electronic design automation (EDA) layout tool for very-large-scale integration (VLSI) integrated circuit (IC) originally written by John Ousterhout...10 KB (1,124 words) - 06:13, 8 May 2024
- In computing, a data source name (DSN, sometimes known as a database source name, though "data sources" can comprise other repositories apart from databases)...4 KB (505 words) - 01:28, 22 June 2023
- Within communication protocols, TLV (type-length-value or tag-length-value) is an encoding scheme used for informational elements. A TLV-encoded data stream...5 KB (606 words) - 14:06, 9 November 2023
- An information school (sometimes abbreviated I-school or iSchool) is a university-level institution committed to understanding the role of information...4 KB (379 words) - 15:59, 2 July 2024
- A cryptographic key is called ephemeral if it is generated for each execution of a key establishment process. In some cases ephemeral keys are used more...2 KB (185 words) - 18:33, 29 April 2024
- ThreeBallot is a voting protocol invented by Ron Rivest and Warren D. Smith in 2006. ThreeBallot is an end-to-end (E2E) auditable voting system that can...11 KB (1,569 words) - 02:05, 2 July 2024