Frontegg’s new Custom Code Prehooks feature (currently in Early Access) addresses the need for customer-defined use cases by allowing developers to execute custom code as part of the authentication process. This innovation empowers organizations to enhance security, customize user experiences, and streamline operations.
Why Custom Code Prehooks Matter
The ability to inject custom code into authentication flows represents a significant advancement in our identity management platform. Custom Code Prehooks enable enterprises to implement additional security checks during the authentication process, such as risk analysis, geofencing, and device security assessments. This ensures that access control measures are dynamically adjusted to meet the highest standards of security and compliance. Moreover, organizations can tailor the login process to offer a more personalized user experience. Depending on factors such as user role, location, or time of access, businesses can customize login prompts, multi-factor authentication requirements, or even redirect users to specific landing pages post-login. This customization is crucial for creating a seamless and engaging user experience.
The Custom Code Prehooks feature also provides IT teams with the flexibility to integrate bespoke logic into the login flow, potentially streamlining operations and reducing the need for manual interventions. This could include automating the provisioning of user-specific resources upon successful authentication or triggering specific actions based on login attempts. By allowing developers to execute custom code, Frontegg offers a powerful tool that extends the functionality of the login process, making it a pillar of our extensibility.
Step-by-Step Guide to Using Custom Code Prehooks
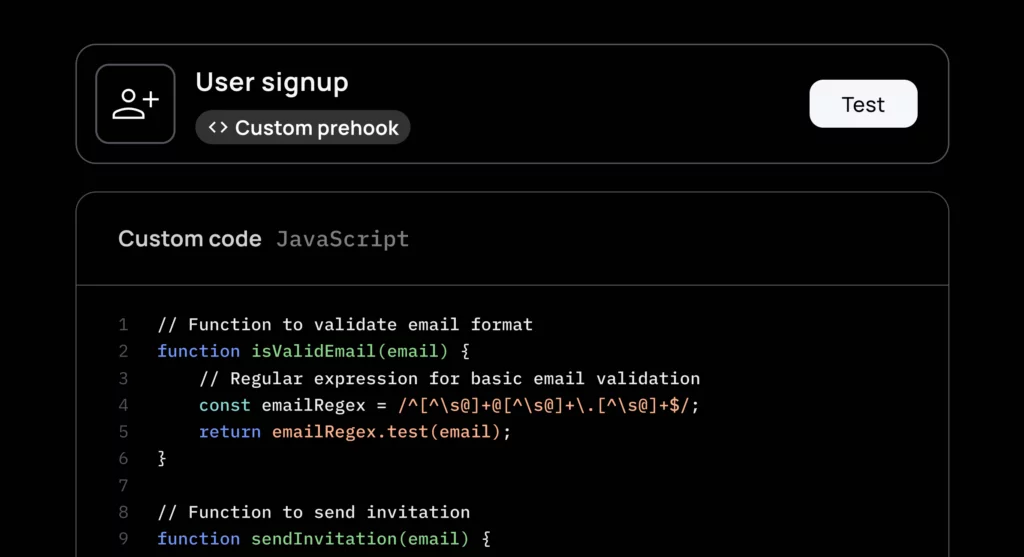
Configuring Custom Code Prehooks within the Frontegg dashboard is straightforward. Begin by logging into your Frontegg dashboard using your credentials. Navigate to the “Prehooks” section and click on “Create Prehook.” Select the trigger event for this prehook to be attached to; for this example, choose the sign-up event. Next, select “Custom Code” to write your own code for Frontegg to execute during the sign-up process. After configuring the initial settings, click “Next” to proceed to the custom code screen.
Here is an example code snippet that blocks all emails using the “gmail.com” domain:
// our array of disallowed emails
const DISALLOWED_DOMAINS = ['gmail.com'];
/**
* Handle the event
* @param {SignUpEventData} eventData - the event details
* @returns {Promise<SignUpHandlerResponse>} event handler response
*/
async function onEvent(eventData) {
// ensure user email is present
if (!eventData.data.user.email) {
// note that userMessage (the second parameter) is displayed in red on the failed sign-up prompt
return { continue: false, verdict: "block", error: { status: 400, message: ["Email is invalid"] }}
}
// ensure a reasonable format for the email
const splitEMail = eventData.data.user.email.split('@');
if (splitEMail.length !== 2) {
// note that userMessage (the second parameter) is displayed in red on the failed sign-up prompt
return { continue: false, verdict: "block", error: { status: 400, message: ["Email is invalid"] }}
}
// if the email domain is not explicitly in our allow list, deny access
const domain = splitEMail[1].toLowerCase();
if (DISALLOWED_DOMAINS.includes(domain)) {
// note that userMessage (the second parameter) is displayed in red on the failed sign-up prompt
return { continue: false, verdict: "block", error: { status: 400, message: ["Email is not
allowed"] }}
}
return { continue: true, verdict: "allow", response: {eventData} }
}
exports.onEvent = onEvent;This code ensures a user email is present, verifies the format, and checks against a list of disallowed domains. Save and enable the prehook, then test the setup by attempting to sign up with a disallowed email domain.
Real-World Applications and Benefits
Custom Code Prehooks can be used to enforce additional security measures such as multi-factor authentication (MFA) or IP address restrictions, providing an extra layer of protection against unauthorized access. By customizing the user onboarding process, businesses can ensure a smooth and personalized experience for new users. This can include guiding users through additional steps or providing tailored content based on their role or location. Additionally, Custom Code Prehooks can automate various operational tasks, such as updating user profiles or triggering notifications, reducing manual workload and improving efficiency.
Heard Enough?
Frontegg’s Custom Code Prehooks feature provides unparalleled flexibility and control over authentication processes. By allowing developers to execute custom code during authentication flows, this feature enhances security, personalizes user experiences, and streamlines operations. Explore Frontegg’s Custom Code Prehooks today and transform your approach to identity and access management.
Ready to enhance your authentication system? Explore Frontegg’s solutions today and see how we can help you create your ideal user management experience.
The Complete Guide to SaaS Multi-Tenant Architecture
Read case study


