Almexoft guarantees maximum security and confidentiality of data, providing it at the level of network, application and physical access to servers.
Data Security
Secure documents processing data encryption, role policy, document registries
Get started-
Roles and permissions
Almeoxft administration system provides a flexible multi-level hierarchy of roles, which can be customized taking into account the organizational company structure and employee positions, and also take into account the functional roles of users. This allows define a set of rules not only for roles, but also for individual users in the system
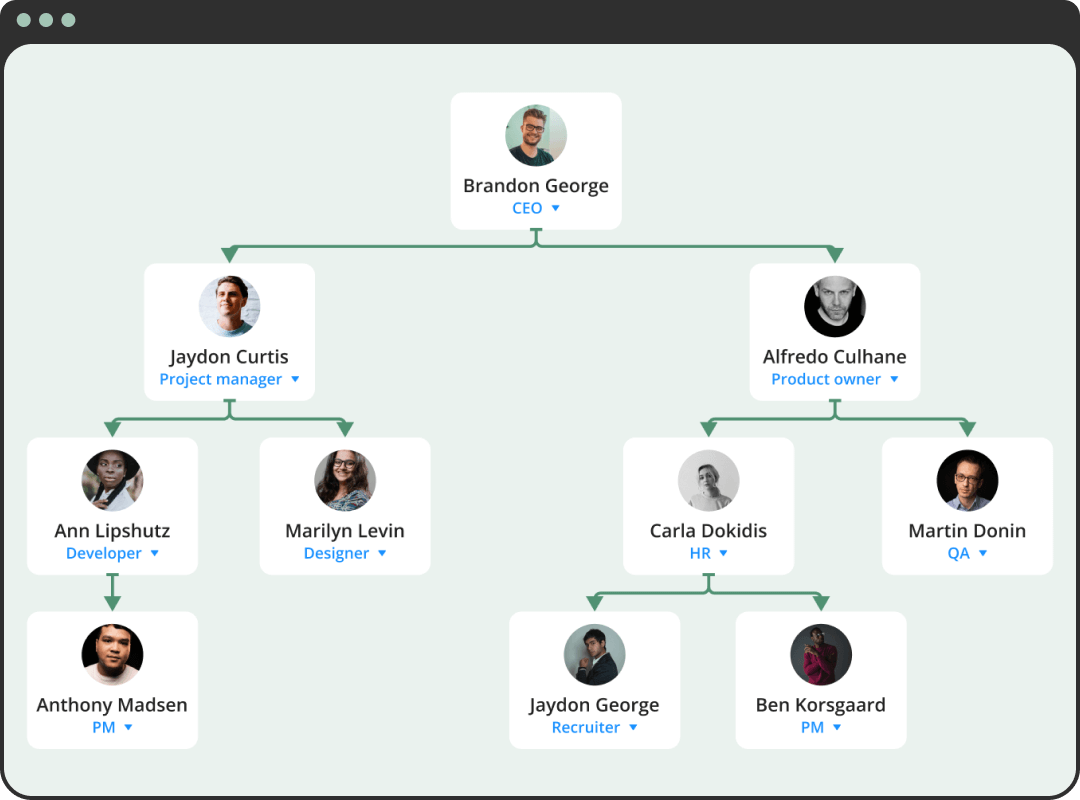
-
Access rights
Almexoft can satisfy any needs for managing access to data and operations in system, starting with providing full access to separate documents for all users and ending with a complete ban with the issue of special permits for certain roles. Administration at level possible objects, records and columns, with the ability to limit access to read, change and delete data
-
Audit Log
Syslog logs critically important actions, providing administrators and experts on information security complete information about transfer of rights to objects, changes in the structure of roles and access levels, successful and unsuccessful attempts authorization, changes in system settings and much more other
-
Data encryption
All information stored in system, can be encrypted by built-in cryptographic algorithm. Files located on server or network storage, in addition to encryption, undergo an additional depersonalization process, which complicates the process of identifying a specific instance or versions. Critical information stored in the database has multiple protection mechanisms, including action protection administrator. Even in the case of direct intervention in structure of the database, the system will detect changes and notify responsible persons about data integrity violation. Encryption is used as for password encryption user, as well as to protect all transmitted data. This key ensures safety during storage, handling and information transfer
Physical security in cloud deployment
Almexoft applications are hosted on the sites of world leaders in the field of cloud infrastructure.
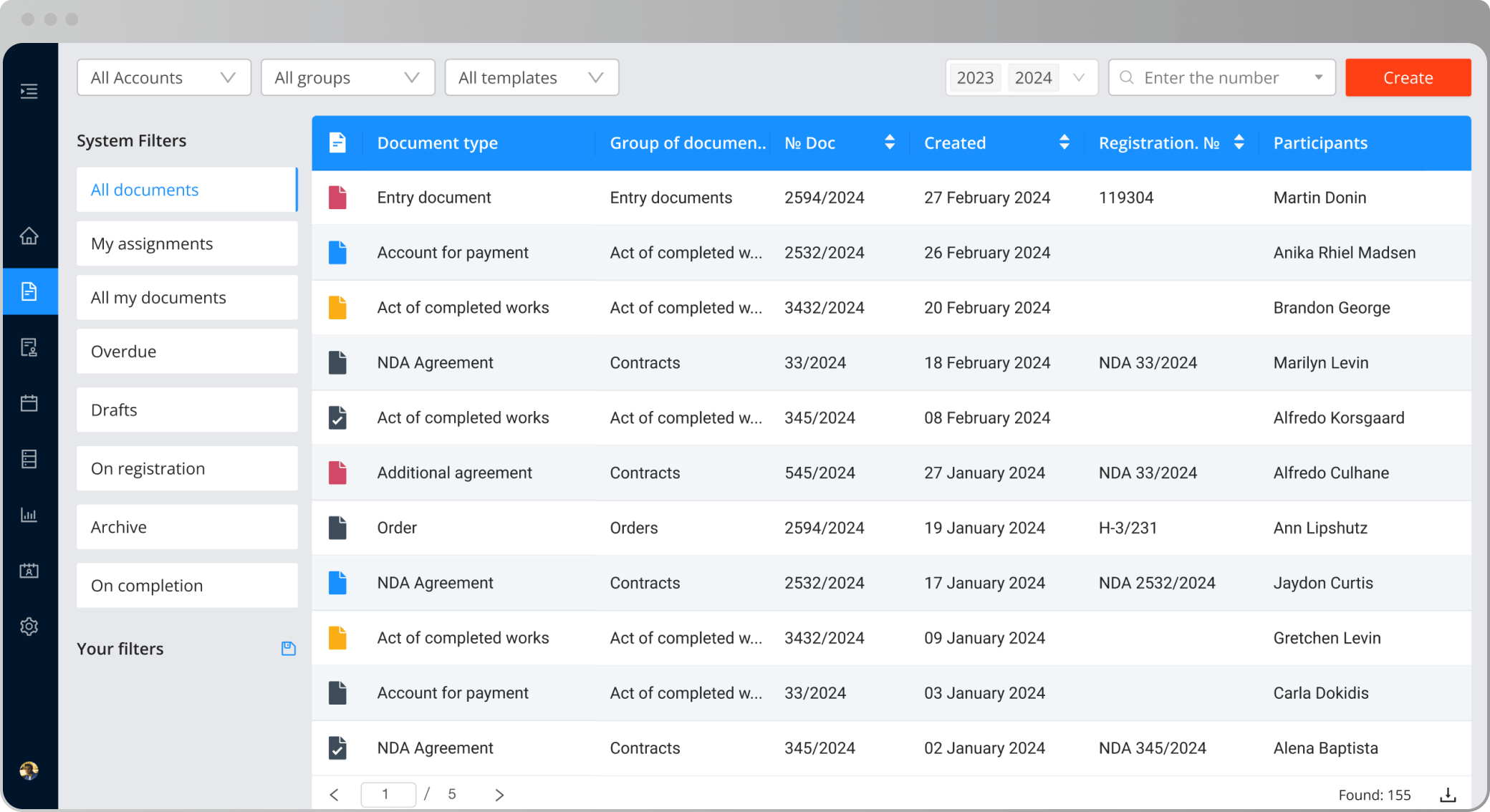
To increase security, all infrastructure elements of the internal structure have multiple copies and backup options. Using multiple data centers provides a level of disaster resilience and independence from one data center.
Optimize your workflow with Almexoft
Get unlimited access to the system for an indefinite period
Start for Free